In several earlier articles, we have mentioned that drivers are a critical component in any operating system. In Windows kernel-level device drivers are loaded to ensure hardware devices can communicate with the operating system. This high level of access by device drivers is secured by a number of safeguards.

Device drivers need to be digitally signed before they are allowed to be installed (even though this can be disabled on some Windows versions). Drivers can also be tested by Microsoft to get the WHQL certification (Windows Hardware Quality Lab). An advantage of WHQL drivers is that they are available through the Windows Update service.
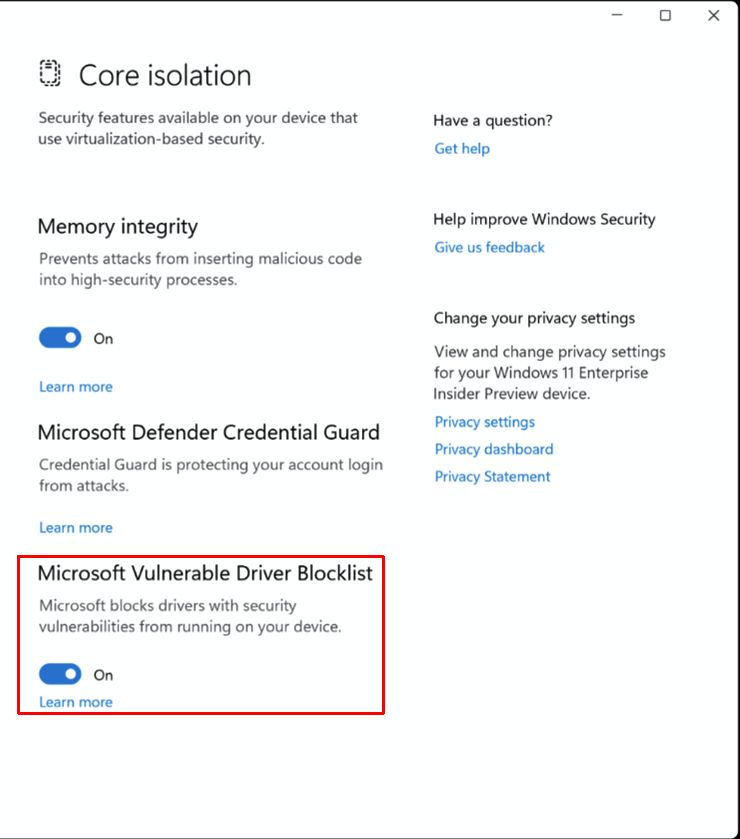
Since the Windows 11 update in 2022, the Hypervisor-Protected Code Integrity (HVCI) security feature prevents vulnerable drivers from being installed. It is important to realize that this is based on a list of known vulnerable Windows drivers. So, anything unknown will not be on the list and still get installed.
Recent Analysis Showed 34 Vulnerable Drivers
It is good to know that there are always people looking for vulnerabilities to help prevent abuse of these vulnerabilities. VMWare recently also released their findings on an automated approach to finding vulnerable Windows drivers using a reverse engineering approach. Details are in their blog post, but the results are quite daunting.
Finding that 34 Windows drivers have vulnerabilities is quite a large number. Most (30) are based on the Windows Driver Model (WDM), while some (4) are using the Windows Driver Framework (WDF). Since some of these drivers include firmware access, one can imagine the kind of access and system takeover that can happen with the exploits of these vulnerabilities.
Solutions to Fix Vulnerable Windows Drivers
Since most of these problems need to be fixed by correcting the flaws, or shortcomings, in the device driver software, vendors must update their drivers and release new versions.
This has happened in 2 of the mentioned cases (Phoenix Technologies fixed the TdkLib64.sys driver and AMD fixed the PDFWKRNL.sys driver).
But there are also suggestions that Microsoft could make changes in how drivers are checked and loaded. The vulnerability list (HVCI) does not seem to be sufficient. It is suggested that preventing signed drivers with a revoked certificate would already block a third of the 34 drivers.
From a user perspective, it is important to keep your drivers up-to-date. Apart from using Windows Update, we recommend you use a program like DriverFinder to check for updates regularly.